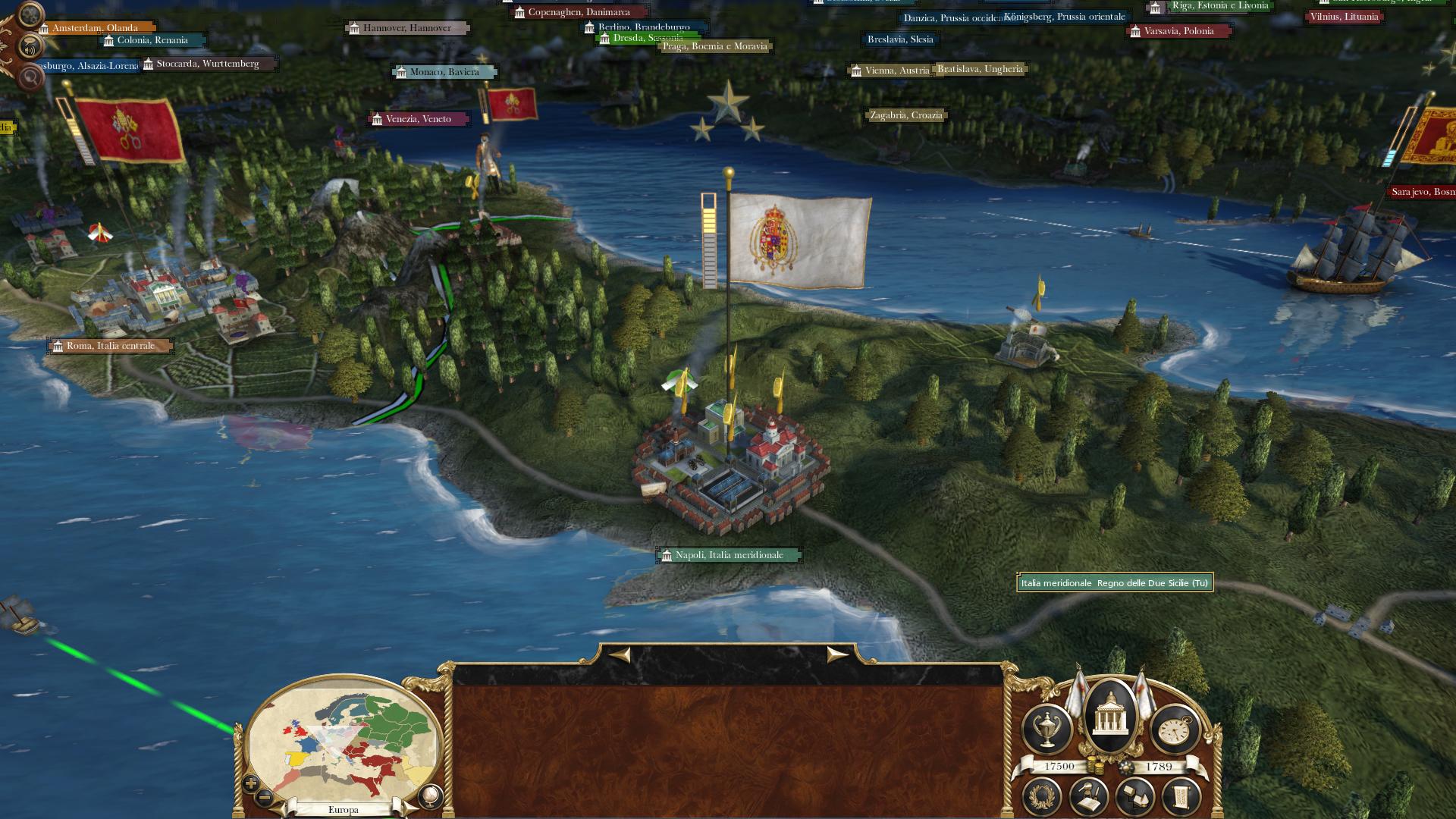
Can You Download Empire Total War Darthmod For Mac

- Can You Download Empire Total War Darthmod For Mac Torrent
- Can You Download Empire Total War Darthmod For Mac Os
- Can You Download Empire Total War Darthmod For Mac Free
- Download Empire Total War Full Game
Causa Belli 2.2 Sep 12 2013 Other 93 comments. Causa Belli is a sub-mod for Darthmod for Empire Total War. It seeks to overhaul the minor factions making them more fun to play or enabling the player. Advice needed on other people who uses this mod. So I'm playing as Louisiana, as I thought it would be easier since I would be mainly fighting against the Indians. I fought a war with the Iroquois.
Total War: Warhammer 2 is officially available on Mac. Feral Interactive released the MacOS and Linux versions of the game earlier today, on November 20, 2018.
Originally developed by Creative Assembly in partnership with Games Workshop, Total War: Warhammer 2 is the follow up to Total War: Warhammer, one of the finest strategy games for Mac.
PS: You may want to check out the brand-new Total War: Three Kingdoms, a game some are calling the best Total War in a decade…
You can download the game from the Humble Store for $59.99.
As with any Total War game, Warhammer 2 features turn-based empire building and real-time tactical battles pitting massive armies full of heroes, spellcasters, and dragons against each other. The campaign picks up after the original Warhammer’s campaign and will take your armies through jungles, deserts, savannahs, and icy mountains.The game has been out for a while on Windows and critics and players all agree: this is an excellent strategy game. The game has an impressive 87 Metascore and 80% Very Positive user reviews on Steam.
Total War: Warhammer 2 on Mac: Everything you need to know
Feral Interactive was in charge of the game’s MacOS and Linux versions, and as was the case with the latest Total War Saga, this is yet another solid Mac port powered by Metal 2.
Powered by Metal 2
As with every other port from Feral Interactive, you can expect all the same features and visuals as the Windows version. Plus, because of the use of Apple’s newest Metal 2 graphics API, performance should be much closer than on Windows than before. Read on for the detailed system requirements but expect Mac benchmarks soon.
Cross-platform multiplayer
Cross-platform multiplayer is the only feature where Mac version and Windows version differ from each other. While Feral did manage to support cross-platform multiplayer between Mac and Linux, the Windows version is excluded. That is definitely a shame as the majority of gamers are on Windows and that means finding online matches will be more difficult.
Hopefully, this will change in the future and Feral will manage to bring cross-platform multiplayer between Mac, Linux, and Windows. This is purely speculation at this time but if Aspyr managed to do it with Civilization 6, anything is possible.
Into Strategy games? These are our favorites:
| Game | ★ Best Overall | Best for MacBook | Best Value |
| Genre | Turn-based | Turn-based | Real-time |
| Release date | 2016 | 2018 | 2015 |
| Metascore | |||
| Our rating | ★★★★☆ Full Review | ★★★★★ Full Review | ★★★★★ Full Review |
| Requirements | High | Low | Low |
| Check Price |
Total War: Warhammer 2 Mac system requirements
These are the game’s official system requirements:
- MacOS 10.14,
- 2.0GHz Intel Core i5 processor
- 8GB RAM
- 2GB Nvidia GeForce GTX 680 MX, AMD R9 M290 or 1.5 Intel Iris Graphics 540 graphics
The game is supported on all these Macs:
- All 13″ MacBook Pros released since 2016
- All 15″ MacBook Pros released since Late 2013 with a 2.3GHz processor or better
- All 21.5″ iMacs released since Late 2017
- All 27″ iMacs released since Late 2013 with a 2GB graphics card or better
- Late 2012 models with a 2GB Nvidia GeForce GTX 680MX graphics card are also supported)
- All 27″ iMac Pros released since Late 2017
- All Mac Pros released since Late 2013
We tested Thrones of Britannia on three different machines for our Mac performance review and the results were encouraging, especially for owners of entry-level MacBook Pros:
You can expect similar levels of performance with Total War: Warhammer 2 on Mac, but we will be testing the game in the coming days and will share the results with you as soon as possible.
Total War: Warhammer 2 Mac Download
Are you a Total War fan? Will you be playing this one? If so, you can go ahead and download the game on Steam or the Humble Store for $59.99.
Updated November 20, 2018: We have updated this post following the announcement that the Mac version was finally released.
TORRENT – FREE DOWNLOAD – CRACKED

Empire: Total War™ – Special Forces Units & Bonus Content – October 5, 2009 – Update The Empire Special Forces units are now available for sale separately as DLC for Empire: Total…
Game Overview
October 5, 2009 – Update The Empire Special Forces units are now available for sale separately as DLC for Empire: Total War. This DLC also includes three additional exclusive units, previously unavailable for sale. ABOUT EMPIRE: TOTAL WAR – SPECIAL FORCES UNITS & BONUS CONTENT In a time when a soldier’s life could be given easily and quickly, it took extreme courage and determination for a true hero to forge a reputation for themselves. Whether through harsh and highly disciplined training, generations of successful military tradition or world-leading technology,…
Empire: Total War™ – Special Forces Units & Bonus Content
CREATIVE ASSEMBLY, Feral Interactive (Mac), Feral Interactive (Linux)
Can You Download Empire Total War Darthmod For Mac Torrent
SEGA, Feral Interactive (Mac), Feral Interactive (Linux)
Can You Download Empire Total War Darthmod For Mac Os
4 Mar, 2009
Can You Download Empire Total War Darthmod For Mac Free
Strategy
DOWNLOAD LINKS
Empire Total War Special Forces Units Bonus Content
Download Empire Total War Full Game
P2P
13.54 GB
TORRENT LINK
System Requirement
Screenshots
Empire: Total War Crack, Empire: Total War DLC Download, Empire: Total War Free Download, Empire: Total War REPACK, Empire: Total War Torrent

Top Ten Free Fps Games For Mac

Games Games Software Software. Browse the newest, top selling and discounted FPS products on Steam New and Trending Top Selling. Free to Play. Dec 18, 2018 Best for: Those who like their FPS games to be as equally funny as they are violent - especially if they don't get attached to their armory, since something more powerful is.
In the war between PC and console gaming, the former is just assumed to always be Windows. But what about Mac? Sure, there isn’t a huge number of games available for Apple’s desktop operating system, but it’s not completely bereft of titles.
In fact, in recent years, some developers like Valve have seemed keen to develop for Mac too. We have already taken a look at the best action games for Mac The 10 Best Action Games You Can Play On Your Mac [MUO Gaming]Getting your frag on with a Mac has never been easy. The most popular action shooters, like most of the Quake games and Call of Duty 4: Modern Warfare have been ported, but as you... Read More , but that covered every single type, from action-adventure to third-person shooters. I wanted to go old-school and discover what first person shooter (FPS) games are available for OS X, and I was quite surprised by the selection…
1. The Orange Box [$19.99]
It’s been six years since Valve released The Orange Box, but there’s no doubt in my mind that this is still the best deal in gaming available. For just $20, you get Half-Life 2, its expansion packs Episode One and Episode Two, the original Portal and Team Fortress 2. Half-Life 2 is among the best games ever made, with a fantastic storyline, gripping gameplay and graphics that still don’t look outdated today. Portal is the finest first-person puzzle game, and Team Fortress 2 is the most fun multiplayer team game you will play. Five high-quality first-person shooters for that price? You’d have to be crazy not to buy that.
2. Borderlands 2 [$29.99]
If you asked me to name the most insane yet fun action game in the past few years, I wouldn’t even need to think for a second to say Borderlands 2. The original Borderlands was a blast and the sequel only improves on that. Playing as one of four “vault hunters”, you have a wide variety of weapons at your disposal, from shotguns to sniper rifles, with plenty of variation in each type. The comic book-like animation style only adds to the charm, taking away realism and putting fun back into the virtual world of guns and gore. No wonder this one made it to our list of the top 10 games on the PlayStation 3 10 Of The Best PS3 Games You Must Play [MUO Gaming]This generation of games consoles is coming to an end, with the Wii U already having arrived to usher in the next-generation, and successors to both the PS3 and Xbox 360 expected in 2013. However,... Read More .
3. Bioshock Infinite [$39.99]
Like the original Bioshock, Bioshock Infinite has one of the best storylines in video games 3 First-Person Shooters That Actually Have Great Stories [MUO Gaming]First-person shooters (or FPS) have long been a genre that is based around competition. Ever since the invention of multiplayer gaming, it only made sense to have shooters as a key genre. I once wrote... Read More . Steampunk has never been executed so well in gaming and Infinite scores high on every aspect: story, gameplay, graphics, voice acting and sound. My personal favorite is hopping on to the Skyline, a single-person railway system which you use to travel around the floating city of Columbia with a hook mechanism. There is nothing as cool as zipping along and shooting enemies. The video above doesn’t do it justice, you need to try it!
4. Call of Duty: Black Ops [$49.99] & Modern Warfare [$19.99]
Call of Duty: Modern Warfare is arguably the best FPS game to be made in the last few years, and definitely the best war game. The franchise kicked away the obsession developers had with World War II shooters and focussed on modern combat instead. The result was one of the most engrossing games ever made with incredible variety in the gameplay, be it as the perfect sniper in Chernobyl, shooting targets on the ground from an airplane, or crawling through enemy lines undetected with your camouflage. Matt wrote a great article on the evolution of the FPS genre Doom Vs. Call Of Duty Modern Warfare - Just How Far Has The FPS Come?First person shooters have been at the forefront of game development since their first incarnation over two decades ago. They combine adrenaline-soaked action with a perspective that provides a great stage for technology; first-person games... Read More from the early days of Doom to COD: Modern Warfare. And after the success of Modern Warfare came a new franchise, Black Ops. The gameplay is similar, so when you’re done with MW, hop on to Black Ops.
5. Left 4 Dead 2 [$19.99]
If you like zombie shooters, Valve’s Left 4 Dead 2 is as good as they get and deservedly finds a spot in the best Xbox 360 games 10 Of The Best Xbox 360 Games You Must Play [MUO Gaming]At this time of year more than any other there will be a host of new console owners getting to grips with their system. And after they get bored of the games bought alongside their... Read More . As a single-player game, L4D2 is a lot of fun, making you attempt to live through a zombie apocalypse as part of a band of four survivors. But where it really shines is in co-op gameplay. Buy it on Steam, connect with other players online and stave off wave after wave of zombies to make the world a safer place once again.
6. Deus Ex Human Revolution [$39.99]
Perfectly marrying the strengths of RPG with those ofthe FPS, it’s a pity that Deus Ex Human Revolution doesn’t get the recognition it deserves (although Dave ranked it as one of the best games of 2011 My 5 Favorite Video Games Of 2011 [MUO Gaming]It is that time of the year. 2011 is over, and 2012 is upon us. The big games from last year are on the shelf, and it is time to talk about our favorite games... Read More ). How you interact with other characters will determine the outcome of the game, and meanwhile, there’s plenty of fighting and stealth action to keep you occupied. And when you throw in a mechanically augmented man as your lead character, there’s always going to be the kind of mayhem you want to be in the middle of!
7.The Darkness 2 [$19.99]
This one is contentious and might just start a flame war in the comments, but The Darkness 2’s gameplay is a blast. Sure, the storyline is silly. Sure, the graphics aren’t the best. Sure, the voice-acting is downright amateurish. But does any of that matter when you’re a paranormal being with a human body appended with two tentacles? You can slice up enemies, grab and toss them, or perform the most gruesome kills once you have them in your power. This one ain’t for kids; I’m not even sure this one is for most adults given the amount of gore involved. But if you like twisted fun, you can’t go wrong with The Darkness 2. Leave your brains at home and just enjoy the crazy gameplay.

Let The Flame War Begin!
Yup, I know I didn’t mention some great FPS games for the Mac. Portal 2, if you can look beyond the “shooter” part, would top this list. Max Payne 3 might look like a third-person shooter, but it plays like an FPS. And then there’s Serious Sam 3: BFE, which is as close as you can get to being Arnold Schwarzenegger. There’s no “definitive list”, so I want to know your picks. What would you remove from this list and what would you replace it with?
Photo Credit: GabrielaP93
The weekend's here and if you're worried about being bored, here are some great FPS games you can play on your Mac.
This time around I'm focusing on some of my favorite first person shooters (FPSs) that are currently available for the Mac platform, ranging in price from free to not free. Locked and loaded? Good. Here we go...
Borderlands 2
- $39.99 - Download now
Every once in a while a sequel comes along that completely eclipses the original game. Such is the case with Borderlands 2, which took everything that was good about the original Borderlands and made it better.
For the uninitiated, Borderlands 2 drops you on the surface of a hostile alien world called Pandora. You're essentially a treasure hunter on a mission. You can choose from one of four different character classes, each with unique abilities, and in a nod to role playing games, you can develop special abilities by assigning skill points that you gain through experience. Borderlands 2 also features a weapons randomizing system that produces an almost unlimited number of variations on handguns, rifles, grenades and other weapons.
A hilarious script and great voice acting provides you with constant laughs through the 30+ hours of single-player fun your first time through (and you will replay this game to get experience with each character class). Add to that fantastic cooperative multiplayer gameplay and downloadable content to extend the game, and you've got a potent mix that will keep you coming back again and again.
Aspyr makes the game available through the Mac App Store and Steam (which we've linked above). Our recommendation is to go for the Steam version so you can get cross-platform multiplayer - Mac App Store downloaders are relegated to Mac-to-Mac play only through Game Center.
BioShock 2
- $24.99 - Download now
Few recent FPS's have had the impact of the BioShock series. The game struck gold for its detailed storyline involving Rapture, a Randian utopia far beneath the surface of the ocean, run amuck. A survival horror game, BioShock 2 puts you in the role of a Big Daddy - a genetically altered human encased in a heavily armored diving suit. Rapture is filled with psychotic and dangerous people who have been altered by a substance that can record their genes, granting them superhuman powers (and, unfortunately, driving them mad).
The game sports multiplayer action too, but unlike Borderlands 2 isn't available from Steam, so the Mac App Store is a safe bet. BioShock 2 is the sequel to the first BioShock, and if you haven't picked that one up, it's definitely worth your time as well, especially at $19.99 price. Both should wet your whistle until BioShock Infinite shows up for the Mac this summer.
Call of Duty 4: Modern Warfare
- $29.99 - Download now
Short of having its superlative sequel on the Mac, Call of Duty 4: Modern Warfare is the next best thing. Sure, it's been around for a while, but this game stands up to the test of time: it's a phenomenal FPS that puts you in the role of U.S. Marines and British SAS commandos as you travel to the U.K, the Middle East, Azerbaijan, Russia and Ukraine on the hunt for international terrorists who plan to detonate a nuclear warhead.
COD4: MW takes a break from past COD games by bringing the action to the modern era, instead of focusing on World War II, which means you have plenty of modern weapons to choose from. It also sports great multiplayer capabilities with plenty of challenges, unlockable perks at matchmaking to make sure you're paired with players of similar abilities.
Team Fortress 2
- Free to play - Download now
A team-based multiplayer first person shooter available through Steam, Team Fortress 2 is almost six years old and still going strong. The game pits two opposing teams against each other in a variety of different modes: Capture the Flag, Control Point, Territorial Control, King of the Hill and more. The play maps vary from the ridiculous to the sublime, and you can choose from nine different player classes, some with offensive capabilities (like the Scout), some better on defense (like the Heavy), and some best for support (such as the Medic).
The game's fun to play not only for its varied gameplay modes and different character classes to master, but also for its cartoon-style art. And it used to be you had to pay for TF2, but Valve made it free to play in 2011. (The company makes money through in-app purchases players make to buy unique equipment and character outfits.)
Counter Strike: Source
- $19.99 - Download now
The original Counter Strike took the world by storm when it was introduced as a mod for Valve Software's legendary game Half-Life. Valve reworked CS as its own independent game using the Source engine (hence the name). It's a team-based first person shooter that emphasizes accomplishing objectives - kill your opponents, rescue hostages and so on. What makes it a bit different than the rest is that when you're shot, you stay dead until the end of the round - no instant respawning.
Twelve years since its first release, Counter Strike still has a huge following and remains ridiculously popular. Last year Valve released Counter Strike: Global Offensive (seen above), so if you've gotten tired of the original, you can immerse yourself in a new game that features updated content from the original, along with new maps, characters and weapons.
Special Mention: Pathways Into Darkness
- Free - Download now
Before Halo, before Myth, before Marathon, way back in 1993, Bungie Software made a name for itself with Mac gamers with one of the most innovative first person shooters we'd ever seen (and really, we hadn't seen a lot of them, but we knew this one was cool). That game was called Pathways Into Darkness.
Man Up Time has resurrected this 20-year-old masterpiece for modern Mac and they've made it absolutely free. Not 'freemium' - there are no in-app purchases you need to make to keep playing. Free. The game traps you in a mysterious pyramid in the Yucatan that threatens the very survival of the Earth. You must descend into its innermost recesses, battling fearsome monsters to save the world.
PID is a game of its era. Its graphics are quaint and primitive, its interface is awkward by modern standards, but it stands out as a period piece worthy of remembering and enjoying. It's a bit of Mac legend. And it's free, so you have nothing to lose but some download bandwidth.
Your go-to first-person shooters?
Those are my favorite FPS games on the Mac right now, but if there are any other can't-miss shooters on your short list, let me know in the comments below. You can never have too much of an awesome thing!
We may earn a commission for purchases using our links. Learn more.
(PRODUCT)REDApple is now redirecting (PRODUCT)RED purchases to COVID‑19 relief fund
Best Free Games For Mac
Now through September 30, Apple is redirecting 100% of a portion of (PRODUCT)RED purchases to the Global Fund’s COVID‑19 Response.

Microsoft Office Per Mac 2011 Service Pack 3

- Microsoft Office Per Mac 2011 Service Pack 3 Error 0x80096004
- Sti Guns
- Microsoft Office Per Mac 2011 Service Pack 3 Download
- Microsoft Office 2011 Mac Upgrade
Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3072620)
Published: July 14, 2015
Version: 1.0
Microsoft Office for Mac Home and Business 2011, Service Pack 1 These license terms are an agreement between Microsoft Corporation (or based on where you live, one of its affiliates) and you. Please read them. They apply to the software that accompanies these license terms, which includes the media on which you received it, if any. Apr 12, 2011 In the Office 2011 SP1 Update (14.1.0) volume window, double-click the Office 2011 SP1 Update (14.1.0) application to start the update process, and then follow the instructions on the screen. If the installation finishes successfully, you can remove the update installer from your hard disk.
Executive Summary
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
This security update is rated Important for all supported editions of the following software:
- Microsoft Excel 2007, Microsoft PowerPoint 2007, Microsoft Word 2007
- Microsoft Office 2010, Microsoft Excel 2010, Microsoft PowerPoint 2010, Microsoft Word 2010
- Microsoft Excel 2013, Microsoft PowerPoint 2013, Microsoft Word 2013
- Microsoft Excel 2013 RT, Microsoft PowerPoint 2013 RT, Microsoft Word 2013 RT
- Microsoft Excel for Mac 2011
- Microsoft Excel Viewer, Microsoft Office Compatibility Pack, Microsoft Word Viewer
- Excel Services on Microsoft SharePoint Server 2007
- Excel Services on Microsoft SharePoint Server 2010
- Excel Services on Microsoft SharePoint Server 2013
For more information, see the Affected Software section.
The security update addresses the vulnerabilities by correcting how Office handles files in memory, by correcting how Excel handles the loading of certain specially crafted binaries, and by correcting how memory information is disclosed. For more information about the vulnerabilities, see the Vulnerability Information section.
For more information about this update, see Microsoft Knowledge Base Article 3072620.
Affected Software
The following software versions or editions are affected. Versions or editions that are not listed are either past their support life cycle or are not affected. To determine the support life cycle for your software version or edition, see Microsoft Support Lifecycle.
Microsoft Office Per Mac 2011 Service Pack 3 Error 0x80096004
Microsoft Office Software
| **Microsoft Office Suites Software** | **Component** | **Maximum Security Impact** | **Aggregate Severity Rating** | **Updates Replaced** |
| **Microsoft Office 2007** | ||||
| Microsoft Office 2007 Service Pack 3 | [Microsoft Excel 2007 Service Pack 3](https://www.microsoft.com/download/details.aspx?familyid=a4dcc4b2-5482-4aad-8ab9-c264107eb838) (2965281) | Remote Code Execution | Important | 2956103 in [MS15-022](https://go.microsoft.com/fwlink/?linkid=526461) |
| Microsoft PowerPoint 2007 Service Pack 3 | [Microsoft PowerPoint 2007 Service Pack 3](https://www.microsoft.com/download/details.aspx?familyid=1c1ae052-724c-4462-a4d6-59a885867bd6) (2965283) | Remote Code Execution | Important | 2899580 in [MS15-022](https://go.microsoft.com/fwlink/?linkid=526461) |
| Microsoft Office 2007 Service Pack 3 | [Microsoft Word 2007 Service Pack 3](https://www.microsoft.com/download/details.aspx?familyid=46307352-a2d0-4431-a22a-b11282f861f8) (3054996) | Remote Code Execution | Important | 2965284 in [MS15-033](https://go.microsoft.com/fwlink/?linkid=532628) |
| **Microsoft Office 2010** | ||||
| Microsoft Office 2010 Service Pack 2 (32-bit editions) | [Microsoft Office 2010 Service Pack 2 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=3d76fd63-1d12-46dc-9245-06639d6c37ac) (3054971) | Remote Code Execution | Important | 3054841 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2010 Service Pack 2 (64-bit editions) | [Microsoft Office 2010 Service Pack 2 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=bd9a8b23-f313-44ec-8efa-f9fec1606100) (3054971) | Remote Code Execution | Important | 3054841 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2010 Service Pack 2 (32-bit editions) | [Microsoft Excel 2010 Service Pack 2 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=627242e3-f079-4dd6-b019-b387f264de77) (3054981) | Remote Code Execution | Important | 3054845 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2010 Service Pack 2 (64-bit editions) | [Microsoft Excel 2010 Service Pack 2 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=610cef0f-fa41-42c1-8ca8-b38fe0086a50) (3054981) | Remote Code Execution | Important | 3054845 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft PowerPoint 2010 Service Pack 2 (32-bit editions) | [Microsoft PowerPoint 2010 Service Pack 2 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=4253bf84-cadf-47c9-9965-b37d12e10d67) (3054963) | Remote Code Execution | Important | 3054835 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft PowerPoint 2010 Service Pack 2 (64-bit editions) | [Microsoft PowerPoint 2010 Service Pack 2 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=7867d3ba-784a-4435-8c6f-cb4dc260fddf) (3054963) | Remote Code Execution | Important | 3054835 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2010 Service Pack 2 (32-bit editions) | [Microsoft Word 2010 Service Pack 2 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=ae88c2b6-730f-4e72-8dd8-d640799d9d62) (3054973) | Remote Code Execution | Important | 3054842 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2010 Service Pack 2 (64-bit editions) | [Microsoft Word 2010 Service Pack 2 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=78d6f668-f355-4298-981e-521edad3a493) (3054973) | Remote Code Execution | Important | 3054842 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| **Microsoft Office 2013** | ||||
| Microsoft Office 2013 Service Pack 1 (32-bit editions) | [Microsoft Excel 2013 Service Pack 1 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=197abd8f-78bf-4da7-bfe4-cb7772ff92d1) (3054949) | Remote Code Execution | Important | 2986216 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | [Microsoft Excel 2013 Service Pack 1 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=a293c5b3-5a93-4233-8ea6-9194da4ff933) (3054949) | Remote Code Execution | Important | 2986216 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft PowerPoint 2013 Service Pack 1 (32-bit editions) | [Microsoft PowerPoint 2013 Service Pack 1 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=1832521b-c1d8-49c3-ad2b-14893f088eb0) (3054999) | Remote Code Execution | Important | 2975816 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft PowerPoint 2013 Service Pack 1 (64-bit editions) | [Microsoft PowerPoint 2013 Service Pack 1 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=51769525-e674-499a-8e3d-ed52764702ed) (3054999) | Remote Code Execution | Important | 2975816 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2013 Service Pack 1 (32-bit editions) | [Microsoft Word 2013 Service Pack 1 (32-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=074c110f-2858-4948-b135-70a70af8f07b) (3054990) | Remote Code Execution | Important | 2965307 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | [Microsoft Word 2013 Service Pack 1 (64-bit editions)](https://www.microsoft.com/download/details.aspx?familyid=e07208aa-7b66-4011-9e69-785d6e56048b) (3054990) | Remote Code Execution | Important | 2965307 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| **Microsoft Office 2013 RT** | ||||
| Microsoft Office 2013 RT Service Pack 1 | Microsoft Excel 2013 RT Service Pack 1 (3054949) [1] | Remote Code Execution | Important | 2986216 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2013 RT Service Pack 1 | Microsoft PowerPoint 2013 RT Service Pack 1 (3054999) [1] | Remote Code Execution | Important | 2975816 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| Microsoft Office 2013 RT Service Pack 1 | Microsoft Word 2013 RT Service Pack 1 (3054990) [1] | Remote Code Execution | Important | 2965307 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| **Microsoft Office for Mac** | ||||
| Microsoft Office for Mac 2011 | [Microsoft Excel for Mac 2011](https://www.microsoft.com/download/details.aspx?familyid=f6d52c5e-2225-42d3-bbf9-37fbdbfbb419) (3073865) | Remote Code Execution | Important | 3048688 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| **Other Office Software** | ||||
| Microsoft Excel Viewer 2007 Service Pack 3 | [Microsoft Excel Viewer 2007 Service Pack 3](https://www.microsoft.com/download/details.aspx?familyid=4f0eabb4-e28b-4767-9dfc-3620c534e8c3) (2965209) | Remote Code Execution | Important | 2956189 in [MS15-022](https://go.microsoft.com/fwlink/?linkid=526461) |
| Microsoft Office Compatibility Pack Service Pack 3 | [Microsoft Office Compatibility Pack Service Pack 3](https://www.microsoft.com/download/details.aspx?familyid=05994e2c-51ef-4fdc-aab3-85b313154c51) (2965208) | Remote Code Execution | Important | 2956106 in [MS15-022](https://go.microsoft.com/fwlink/?linkid=526461) |
| Microsoft Word Viewer | [Microsoft Word Viewer](https://www.microsoft.com/download/details.aspx?familyid=3ec20892-a288-426a-a624-3ecd100cecf5) (3054958) | Remote Code Execution | Important | 2965289 in [MS15-033](https://go.microsoft.com/fwlink/?linkid=532628) |
Microsoft Office Services and Web Apps
| **Microsoft Office Services and Web Apps** | **Component** | **Maximum Security Impact** | **Aggregate Severity Rating** | **Updates Replaced** |
| **Microsoft SharePoint Server 2007** | ||||
| Microsoft SharePoint Server 2007 Service Pack 3 (32-bit editions) | [Excel Services](https://www.microsoft.com/download/details.aspx?familyid=82504d36-6b1c-4683-a9ff-6ea69b8452ed) (2837612) | Remote Code Execution | Important | 2827327 in [MS13-084](https://go.microsoft.com/fwlink/?linkid=324028) |
| Microsoft SharePoint Server 2007 Service Pack 3 (64-bit editions) | [Excel Services](https://www.microsoft.com/download/details.aspx?familyid=bd4769dc-646d-4899-a1c2-0c18dee426e3) (2837612) | Remote Code Execution | Important | 2827327 in [MS13-084](https://go.microsoft.com/fwlink/?linkid=324028) |
| **Microsoft SharePoint Server 2010** | ||||
| Microsoft SharePoint Server 2010 Service Pack 2 | [Excel Services](https://www.microsoft.com/download/details.aspx?familyid=e4740c9c-7bc4-4acd-93ec-b796f953e1e1) (3054968) | Remote Code Execution | Important | 3054839 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
| **Microsoft SharePoint Server 2013** | ||||
| Microsoft SharePoint Server 2013 Service Pack 1 | [Excel Services](https://www.microsoft.com/download/details.aspx?familyid=9a27ae56-9e63-4ae9-b2fb-2bc5e9bf0c00) (3054861) | Remote Code Execution | Important | 3039725 in [MS15-046](https://go.microsoft.com/fwlink/?linkid=533724) |
Update FAQ
Sti Guns

I have Microsoft Word 2010 installed. Why am I not being offered the 3054971 update?
The 3054971 update only applies to systems running specific configurations of Microsoft Office 2010. Some configurations will not be offered the update.
I am being offered this update for software that is not specifically listed in the Affected Software table. Why am I being offered this update?
When updates address vulnerable code that exists in a component that is shared between multiple Microsoft Office products or shared between multiple versions of the same Microsoft Office product, the update is considered to be applicable to all supported products and versions that contain the vulnerable component.
For example, when an update applies to Microsoft Office 2007 products, only Microsoft Office 2007 may be specifically listed in the Affected Software table. However, the update could apply to Microsoft Word 2007, Microsoft Excel 2007, Microsoft Visio 2007, Microsoft Compatibility Pack, Microsoft Excel Viewer, or any other Microsoft Office 2007 product that is not specifically listed in the Affected Software table.
For example, when an update applies to Microsoft Office 2010 products, only Microsoft Office 2010 may be specifically listed in the Affected Software table. However, the update could apply to Microsoft Word 2010, Microsoft Excel 2010, Microsoft Visio 2010, Microsoft Visio Viewer, or any other Microsoft Office 2010 product that is not specifically listed in the Affected Software table.
For example, when an update applies to Microsoft Office 2013 products, only Microsoft Office 2013 may be specifically listed in the Affected Software table. However, the update could apply to Microsoft Word 2013, Microsoft Excel 2013, Microsoft Visio 2013, or any other Microsoft Office 2013 product that is not specifically listed in the Affected Software table.
Severity Ratings and Vulnerability Identifiers
The following severity ratings assume the potential maximum impact of the vulnerability. For information regarding the likelihood, within 30 days of this security bulletin's release, of the exploitability of the vulnerability in relation to its severity rating and security impact, please see the Exploitability Index in the July bulletin summary.
Microsoft Office Software
| **Vulnerability Severity Rating and Maximum Security Impact by Affected Software** | |||||||||
| **Affected Software** | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2376**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2376) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2377**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2377) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2379**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2379) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2380**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2380) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2415**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2415) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2424**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2424) | [**Microsoft Excel ASLR Bypass Vulnerability – CVE-2015-2375**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2375) | [**Microsoft Excel DLL Remote Code Execution Vulnerability – CVE-2015-2378**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2378) | **Aggregate Severity Rating** |
| **Microsoft Office 2007** | |||||||||
| Microsoft Excel 2007 Service Pack 3 | **Important**Remote Code Execution (2965281) | **Important**Remote Code Execution (2965281) | Not applicable | Not applicable | **Important**Remote Code Execution (2965281) | Not applicable | Not applicable | **Important**Remote Code Execution (2965281) | **Important** |
| Microsoft PowerPoint 2007 Service Pack 3 | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (2965283) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2007 Service Pack 3 | Not applicable | Not applicable | **Important**Remote Code Execution (3054996) | **Important**Remote Code Execution (3054996) | Not applicable | **Important**Remote Code Execution (3054996) | Not applicable | Not applicable | **Important** |
| **Microsoft Office 2010** | |||||||||
| Microsoft Office 2010 Service Pack 2 (32-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054971) | **Important**Remote Code Execution (3054971) | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| Microsoft Office 2010 Service Pack 2 (64-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054971) | **Important**Remote Code Execution (3054971) | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| Microsoft Excel 2010 Service Pack 2 (32-bit editions) | **Important**Remote Code Execution (3054981) | **Important**Remote Code Execution (3054981) | Not applicable | Not applicable | **Important**Remote Code Execution (3054981) | Not applicable | **Important**Information Disclosure (3054981) | **Important**Remote Code Execution (3054981) | **Important** |
| Microsoft Excel 2010 Service Pack 2 (64-bit editions) | **Important**Remote Code Execution (3054981) | **Important**Remote Code Execution (3054981) | Not applicable | Not applicable | **Important**Remote Code Execution (3054981) | Not applicable | **Important**Information Disclosure (3054981) | **Important**Remote Code Execution (3054981) | **Important** |
| Microsoft PowerPoint 2010 Service Pack 2 (32-bit editions) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (3054963) | Not applicable | Not applicable | **Important** |
| Microsoft PowerPoint 2010 Service Pack 2 (64-bit editions) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (3054963) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2010 Service Pack 2 (32-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054973) | **Important**Remote Code Execution (3054973) | Not applicable | **Important**Remote Code Execution (3054973) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2010 Service Pack 2 (64-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054973) | **Important**Remote Code Execution (3054973) | Not applicable | **Important**Remote Code Execution (3054973) | Not applicable | Not applicable | **Important** |
| **Microsoft Office 2013** | |||||||||
| Microsoft Excel 2013 Service Pack 1 (32-bit editions) | **Important**Remote Code Execution (3054949) | **Important**Remote Code Execution (3054949) | Not applicable | Not applicable | **Important**Remote Code Execution (3054949) | Not applicable | **Important**Information Disclosure (3054949) | Not applicable | **Important** |
| Microsoft Excel 2013 Service Pack 1 (64-bit editions) | **Important**Remote Code Execution (3054949) | **Important**Remote Code Execution (3054949) | Not applicable | Not applicable | **Important**Remote Code Execution (3054949) | Not applicable | **Important**Information Disclosure (3054949) | Not applicable | **Important** |
| Microsoft PowerPoint 2013 Service Pack 1 (32-bit editions) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (3054999) | Not applicable | Not applicable | **Important** |
| Microsoft PowerPoint 2013 Service Pack 1 (64-bit editions) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (3054999) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2013 Service Pack 1 (32-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054990) | **Important**Remote Code Execution (3054990) | Not applicable | **Important**Remote Code Execution (3054990) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2013 Service Pack 1 (64-bit editions) | Not applicable | Not applicable | **Important**Remote Code Execution (3054990) | **Important**Remote Code Execution (3054990) | Not applicable | **Important**Remote Code Execution (3054990) | Not applicable | Not applicable | **Important** |
| **Microsoft Office 2013 RT** | |||||||||
| Microsoft Excel 2013 RT Service Pack 1 | **Important**Remote Code Execution (3054949) | **Important**Remote Code Execution (3054949) | Not applicable | Not applicable | **Important**Remote Code Execution (3054949) | Not applicable | **Important**Information Disclosure (3054949) | Not applicable | **Important** |
| Microsoft PowerPoint 2013 RT Service Pack 1 | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (3054999) | Not applicable | Not applicable | **Important** |
| Microsoft Word 2013 RT Service Pack 1 | Not applicable | Not applicable | **Important**Remote Code Execution (3054990) | **Important**Remote Code Execution (3054990) | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| **Microsoft Office for Mac** | |||||||||
| Microsoft Office for Mac 2011 | **Important**Remote Code Execution (3073865) | Not applicable | **Important**Remote Code Execution (3073865) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| **Other Office Software** | |||||||||
| Microsoft Excel Viewer 2007 Service Pack 3 | **Important**Remote Code Execution (2965209) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Remote Code Execution (2965209) | **Important** |
| Microsoft Office Compatibility Pack Service Pack 3 | **Important**Remote Code Execution (2965208) | **Important**Remote Code Execution (2965208) | Not applicable | Not applicable | **Important**Remote Code Execution (2965208) | Not applicable | Not applicable | **Important**Remote Code Execution (2965208) | **Important** |
| Microsoft Word Viewer | Not applicable | Not applicable | **Important**Remote Code Execution (3054958) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
Microsoft Office Services and Web Apps
| **Vulnerability Severity Rating and Maximum Security Impact by Affected Software** | |||||||||
| **Affected Software** | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2376**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2376) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2377**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2377) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2379**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2379) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2380**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2380) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2415**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2415) | [**Microsoft Office Memory Corruption Vulnerability – CVE-2015-2424**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2424) | [**Microsoft Excel ASLR Bypass Vulnerability – CVE-2015-2375**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2375) | [**Microsoft Excel DLL Remote Code Execution Vulnerability – CVE-2015-2378**](https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-2378) | **Aggregate Severity Rating** |
| **Microsoft SharePoint Server 2007** | |||||||||
| Excel Services on Microsoft SharePoint Server 2007 Service Pack 3 (32-bit editions) | **Important**Remote Code Execution (2837612) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| Excel Services on Microsoft SharePoint Server 2007 Service Pack 3 (64-bit editions) | **Important**Remote Code Execution (2837612) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important** |
| **Microsoft SharePoint Server 2010** | |||||||||
| Excel Services on Microsoft SharePoint Server 2010 Service Pack 2 | **Important**Remote Code Execution (3054968) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Information Disclosure (3054968) | Not applicable | **Important** |
| **Microsoft SharePoint Server 2013** | |||||||||
| Excel Services on Microsoft SharePoint Server 2013 Service Pack 1 | **Important**Remote Code Execution (3054861) | Not applicable | Not applicable | Not applicable | Not applicable | Not applicable | **Important**Information Disclosure (3054861) | Not applicable | **Important** |
Vulnerability Information
Multiple Microsoft Office Memory Corruption Vulnerabilities
Remote code execution vulnerabilities exist in Microsoft Office software when the Office software fails to properly handle objects in memory.
Exploitation of these vulnerabilities requires that a user open a specially crafted file with an affected version of Microsoft Office software. In an email attack scenario an attacker could exploit the vulnerabilities by sending the specially crafted file to the user and convincing the user to open the file. In a web-based attack scenario an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerabilities. An attacker would have no way to force users to visit the website. Instead, an attacker would have to convince users to click a link, typically by way of an enticement in an email or Instant Messenger message.
An attacker who successfully exploited these vulnerabilities could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
The security update addresses the vulnerabilities by correcting how Microsoft Office handles files in memory.
Microsoft Office Per Mac 2011 Service Pack 3 Download
The following tables contain links to the standard entry for each vulnerability in the Common Vulnerabilities and Exposures list:
| Vulnerability title | CVE number | Publicly Disclosed | Exploited |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2376 | No | No |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2377 | No | No |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2379 | No | No |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2380 | No | No |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2415 | No | No |
| Microsoft Office Memory Corruption Vulnerability | CVE-2015-2424 | No | Yes |
Microsoft Office 2011 Mac Upgrade
### Mitigating Factors Microsoft has not identified any [mitigating factors](https://technet.microsoft.com/library/security/dn848375.aspx) for these vulnerabilities. ### Workarounds Microsoft has not identified any [workarounds](https://technet.microsoft.com/library/security/dn848375.aspx) for these vulnerabilities. Microsoft Excel ASLR Bypass Vulnerability - CVE-2015-2375 --------------------------------------------------------- A security feature bypass vulnerability exists in Microsoft Excel when memory is released in an unintended manner. The vulnerability could allow an attacker to bypass the [Address Space Layout Randomization (ASLR)](https://technet.microsoft.com/en-us/library/security/dn848375.aspx) security feature, and potentially allow remote code execution. The security feature bypass by itself does not allow arbitrary code execution. However, an attacker could use this security feature bypass vulnerability in conjunction with another vulnerability, such as a remote code execution vulnerability, to run arbitrary code. An attacker who successfully exploited this vulnerability could bypass the ASLR security feature. Exploitation of this vulnerability requires that a user open a specially crafted Excel (.xls) file with an affected version of Microsoft Office software. In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted Excel (.xls) file to the user and then convincing the user to open the file in an affected version of Microsoft Office software. In a web-based attack scenario, an attacker could host a website that contains a file that is used to attempt to exploit the vulnerability. In addition, compromised websites and websites that accept or host user-provided content could contain specially crafted content that could exploit this vulnerability. An attacker would have no way to force users to visit a specially crafted website. Instead, an attacker would have to convince them to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes them to the attacker's site, and then convince them to open the specially crafted Excel (.xls) file in an affected version of Microsoft Office software. The update addresses the vulnerability by correcting how memory information is disclosed. Microsoft received information about the vulnerability through coordinated vulnerability disclosure. When this security bulletin was issued, Microsoft had not received any information to indicate that this vulnerability had been publicly used to attack customers. ### Mitigating Factors Microsoft has not identified any [mitigating factors](https://technet.microsoft.com/library/security/dn848375.aspx) for this vulnerability. ### Workarounds Microsoft has not identified any [workarounds](https://technet.microsoft.com/library/security/dn848375.aspx) for this vulnerability. Microsoft Excel DLL Remote Code Execution Vulnerability - CVE-2015-2378 ----------------------------------------------------------------------- A remote code execution vulnerability exists when Microsoft Excel improperly handles the loading of dynamic link library (DLL) files. An attacker who successfully exploited the vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. To exploit the vulnerability, an attacker would first have to place a specially crafted DLL file in the target user’s current working directory. The attacker would then have to convince the user to launch a program designed to load a trusted DLL, but which mistakenly loads the malicious specially crafted DLL file. The update addresses the vulnerability by correcting how Excel handles the loading of certain specially crafted binaries. Microsoft received information about the vulnerability through coordinated vulnerability disclosure. When this security bulletin was issued, Microsoft had not received any information to indicate that this vulnerability had been publicly used to attack customers. ### Mitigating Factors Microsoft has not identified any [mitigating factors](https://technet.microsoft.com/library/security/dn848375.aspx) for this vulnerability. ### Workarounds Microsoft has not identified any [workarounds](https://technet.microsoft.com/library/security/dn848375.aspx) for this vulnerability. Security Update Deployment -------------------------- For Security Update Deployment information, see the Microsoft Knowledge Base article referenced in the Executive Summary. Acknowledgments --------------- Microsoft recognizes the efforts of those in the security community who help us protect customers through coordinated vulnerability disclosure. See [Acknowledgments](https://technet.microsoft.com/library/security/dn903755.aspx) for more information. Disclaimer ---------- The information provided in the Microsoft Knowledge Base is provided 'as is' without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including the warranties of merchantability and fitness for a particular purpose. In no event shall Microsoft Corporation or its suppliers be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Microsoft Corporation or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing limitation may not apply. Revisions --------- - V1.0 (July 14, 2015): Bulletin published. *Page generated 2015-07-14 13:22Z-07:00.*
Virtual Dj 8 Skins

Virtual dj 8 skins free download - VirtualDJ 2020, VirtualDJ 2020, Dj Mixer for Windows 8, and many more programs. Virtual DJ Mix song is a Virtual mixing software studio and easy to use. SKIN: Serato Scratch Live 2.8.0 Full Panel Skin for Virtual DJ 8. DJ Tools Skins. SKIN: SERATO DJ 1.9 Skin For Virtual DJ 8 Extended & Customized by DJ Rogz. DJ Tools Skins 1 year ago. DJ Tools Skins. SKIN: Virtual DJ 8 Pro Skin by DJ Rogz. DJ Tools Skins 1 year ago. DJ Tools Skins. Aug 28, 2018 Skin Personalizable para Virtual Dj 8 - Duration: 9:32. Alejo Lopez 68,329 views.
Virtual Dj Serato Download Free

Most Popular | New Arrivals | |
1024x768 Nb downloads: 1 (1 617) | 1280 X 800 Nb downloads: 1 (6 890) | 1280x800 & 1366x768 & 1920x1080 Nb downloads: 0 (824) |
1280x768 Nb downloads: 1 (496) | 1280x800 Nb downloads: 1 (7 548) | 1024x768 Nb downloads: 1 (659) |
Author: Lady Cameron Created for VirtualDJ version 3.0 | EKS XP10 Nb downloads: 1 (1 964) | 1920 X 1080 Nb downloads: 2 (2 118) |
1024:768 Nb downloads: 1 (3 978) | 1920x1080 Nb downloads: 1 (1 234) | 1440X900 Nb downloads: 2 (6 714) |
1280X 768 Nb downloads: 1 (3 532) | 1024x768 Nb downloads: 1 (51 944) | 1400 X 1000 Nb downloads: 0 (1 333) |
1024x768 - 1280x960 Nb downloads: 1 (2 994) | 1280x800 Nb downloads: 1 (27 530) | 1024 X 600 Nb downloads: 1 (3 083) |
1280x800 Nb downloads: 1 (103 777) | iPad default skin 1.0 Author: Stephane Clavel Created for VirtualDJ version 7.0.2 | Sweet Scratch x4 v.2.3 Author: the SOUND INSURGENT Created for VirtualDJ version 7 |
KoreDJ Full HD 1.0 Author: kored Created for VirtualDJ version 6/7 | i-BeDJ 7.0.5 Author: X-elot Created for VirtualDJ version All | djjb's v7 touch. The original 2.0 Author: djjb Created for VirtualDJ version 7 |
VirtualTouch Double 1.0 Author: djdad Created for VirtualDJ version 7.x | DASHLIGHT2.0 1.25 Author: cbgraphix Created for VirtualDJ version 7.x | Kitzunae 1.1.0 Author: grad3zer0 Created for VirtualDJ version 7 |
GROM 4Decks 1.0 Author: djdad Created for VirtualDJ version 7.x | iControl 2 1 Author: Simon Bailey Created for VirtualDJ version 7 | CDJ EXTENSION 2.0 Author: ianmelville Created for VirtualDJ version 7.0.5b |
Virtual Dj 8 Skins Free Download For Pc

Teamviewer Für Mac Free Download

Remote access software can be a cost-effective way of enjoying a secure connection between networks and devices.
- Teamviewer 11 For Mac Free Download
- Teamviewer 11 For Mac Download
- Teamviewer 13 For Mac Free Download
- Teamviewer For Mac Os X 10.4
- Teamviewer 10 For Mac
- Teamviewer 7 For Mac Free Download
Mar 15, 2020 The 15.3.2682 version of TeamViewer for Mac is available as a free download on our website. The most popular versions among the application users are 10.0, 9.0 and 7.0. This Mac download was checked by our antivirus and was rated as clean. This software for Mac OS X is a product of TeamViewer GmbH.
Privacy PolicyRemote access software allows local users to establish a connection with a remote device or network. The software can be installed directly onto a device and accessed over the internet at any time. Widely used by employees at large and medium-sized companies who run on a corporate network, remote access facilitates improved processes for IT support workers and enables more streamlined cooperation among teams working in different locations. Through the use of remote access software, important resources such as files, documents, and even software that is saved onto the company network can be accessed no matter where you are.
Remote access software works by creating a connection between the local and host devices. To establish a remote access connection, both machines must be powered on; they must have a good internet connection; and the software in question must be installed. A new session is possible once you run the remote software at both ends of the connection. An access code is generated that will be used to authenticate your login from the local device to the remote device. Once this is complete, the two machines are connected via a secure desktop sharing network that grants you full control over the remote device and all of its resources.
Remotely accessing PC resources is important for both small and large businesses. It gives employees instant access to important resources whenever they need them. Suitable for tech support staff, managed service providers, and anyone tasked with troubleshooting technical issues, remote desktop software can transform your IT maintenance process overnight. With features such as instant access to files, seamless resource sharing, and secure connections, remote access tools have never been simpler to use.
For small businesses looking for a cost-effective first step into the world of remote access solutions, or perhaps those interested in a trial phase first, there are of course free remote access software programs available. Additionally, with certain operating systems there are built-in remote access tools that provide a few basic features, even though they remain somewhat limited in comparison to those offered as paid software. The free remote access software solutions are a great way to determine which features your business requires most.
One of the most appealing factors of remote software is not just its cost effectiveness, but also its ease of use. Ideal for both first time users and IT novices alike, the software solutions provide users with the freedom to experiment with the tool before acquiring more comprehensive software and paying for the extended features.
Another option is open source or distribution-free remote software. This may be more suited to IT experts who seek to modify or customise the software themselves to best suit the needs and requirements of their businesses.
Teamviewer 11 For Mac Free Download
Alternatively, another option is to explore the built-in capabilities offered by certain operating systems, many of which include free remote access software and allow certain remote functions. Windows, for example, offers some intuitive remote desktop tools that enable IT support technicians to perform certain tasks remotely.
The tool itself is called Windows Remote Desktop and allows users to access system properties, reboot computers, view event logs, and manage Windows processes – no matter where they are located. While built-in remote access tools offer a number of helpful features, they are often limited in their cross-platform compatibility and security.
Remote access software allows local users to establish a connection with a remote device or network. The software can be installed directly onto a device and accessed over the internet at any time. Widely used by employees at large and medium-sized companies who run on a corporate network, remote access facilitates improved processes for IT support workers and enables more streamlined cooperation among teams working in different locations. Through the use of remote access software, important resources such as files, documents, and even software that is saved onto the company network can be accessed no matter where you are.
Remote access software works by creating a connection between the local and host devices. To establish a remote access connection, both machines must be powered on; they must have a good internet connection; and the software in question must be installed. A new session is possible once you run the remote software at both ends of the connection. An access code is generated that will be used to authenticate your login from the local device to the remote device. Once this is complete, the two machines are connected via a secure desktop sharing network that grants you full control over the remote device and all of its resources.
Remotely accessing PC resources is important for both small and large businesses. It gives employees instant access to important resources whenever they need them. Suitable for tech support staff, managed service providers, and anyone tasked with troubleshooting technical issues, remote desktop software can transform your IT maintenance process overnight. With features such as instant access to files, seamless resource sharing, and secure connections, remote access tools have never been simpler to use.
For small businesses looking for a cost-effective first step into the world of remote access solutions, or perhaps those interested in a trial phase first, there are of course free remote access software programs available. Additionally, with certain operating systems there are built-in remote access tools that provide a few basic features, even though they remain somewhat limited in comparison to those offered as paid software. The free remote access software solutions are a great way to determine which features your business requires most.
One of the most appealing factors of remote software is not just its cost effectiveness, but also its ease of use. Ideal for both first time users and IT novices alike, the software solutions provide users with the freedom to experiment with the tool before acquiring more comprehensive software and paying for the extended features.
Another option is open source or distribution-free remote software. This may be more suited to IT experts who seek to modify or customise the software themselves to best suit the needs and requirements of their businesses.
Alternatively, another option is to explore the built-in capabilities offered by certain operating systems, many of which include free remote access software and allow certain remote functions. Windows, for example, offers some intuitive remote desktop tools that enable IT support technicians to perform certain tasks remotely.
The tool itself is called Windows Remote Desktop and allows users to access system properties, reboot computers, view event logs, and manage Windows processes – no matter where they are located. While built-in remote access tools offer a number of helpful features, they are often limited in their cross-platform compatibility and security.
A flexible approach
Free remote access tools allow users to experiment with the various features offered. When the time comes to opt in to a paid solution, users know exactly which features they require.
Easy access
The accessibility provided by free remote access software is unbeatable: you can access data or software any time, any place, anywhere, without spending a penny.
Lower costs
Remote access solutions cut costs across the board. There is no need to invest in as many servers, staff, or devices to keep your business running. In addition travel costs are reduced significantly.
Online Security
Guaranteeing the security of remote access software is a top priority for any company. Consequently, most modern software programs have various built-in features to ensure that only authorised personnel have access to specific devices and resources. These include:
- Two-factor authentication, which requires a unique code generated on an app on your secondary mobile device in order to login.
- End-to-end encryption, which ensures that only those communicating with each other can decipher the messages being sent.
- Exponetial latency increases between connection attempts for protection against brute-force attacks.
In addition, you can retain authorisation rights to specify users who are allowed to access certain resources using blacklist and whitelist functions.
Teamviewer 11 For Mac Download
How do I remotely access another computer?
Follow the steps below to remotely access a partner’s computer:
- Ensure the TeamViewer software is installed on both your computer and your partner’s computer, and create a TeamViewer account.
- Open TeamViewer and log in to your account.
- Ask your partner for their ID (found in the “Allow Remote Control” section of the TeamViewer interface).
- Enter this ID into the “Partner ID” field (under “Control Remote Computer”) and click “CONNECT”.
- You can now remotely access and control your partner’s computer.
Is remote access software safe?
The security of your data is paramount to TeamViewer. In order to make sure that only authorised users have access, TeamViewer uses two-factor authentication, an extra layer of security that prompts the user to enter a code on top of their password before they can log in. The time increases between failed login attempts to prevent brute-force attacks. End-to-end encryption means that only the sender and the intended recipient can read the messages being sent.
Teamviewer 13 For Mac Free Download
What are the benefits of remote access?
Remote access with TeamViewer allows you to access resources and carry out tasks on a device without having to be physically present. The flexibility this enables is hugely beneficial for facilitating working from home, since employees have full access to company servers and collaboration tools. Remote access also helps streamline IT support processes, allowing teams to log in to the corporate network remotely to perform maintenance and system updates.
Who is remote access software suitable for?
Remotely accessing devices is advantageous for all kinds of companies, since it enables a modern working environment. For instance, employees are able to quickly log in and complete tasks from home, and IT support teams can troubleshoot on the go. Remote access is also a great option for start-ups without a permanent office, or those that rely mostly on remote workers.
TeamViewer for Windows
- Establish incoming and outgoing connections between devices
- Real-time remote access and support
- Collaborate online, participate in meetings, and chat with others
- Start using TeamViewer for free immediately after downloading
Buy a license in order to use even more TeamViewer features
Check out additional TeamViewer remote desktop support and collaboration downloads
Immediate assistance:
TeamViewer QuickSupport
Optimized for instant remote desktop support, this small customer module does not require installation or administrator rights — simply download, double click, and give the provided ID and password to your supporter.
Join a meeting:
TeamViewer QuickJoin
Easily join meetings or presentations and collaborate online with this customer module. It requires no installation or administrator rights — just download, double click, and enter the session data given to you by your meeting organizer.
TeamViewer MSI package
Teamviewer For Mac Os X 10.4

TeamViewer MSI is an alternative installation package for the full version of TeamViewer or for TeamViewer Host. TeamViewer MSI is used to deploy TeamViewer via Group Policy (GPO) in an Active Directory domain.
To download, log in to your account in the Management Console; go to the Design & Deploy section; and create a custom host or edit your existing custom host. In the customization menu, you will have the option to download your MSI package.
Please note: TeamViewer MSI is only available with a Corporate license.
TeamViewer Portable
Teamviewer 10 For Mac
TeamViewer Portable generally comprises all the features of the full version of TeamViewer without the need to install anything. Instead, TeamViewer portable runs directly from a USB stick or a CD — TeamViewer Portable is the perfect solution when you are on the road and using different computers.
Unattended access:
TeamViewer Host
TeamViewer Host is used for 24/7 access to remote computers, which makes it an ideal solution for uses such as remote monitoring, server maintenance, or connecting to a PC or Mac in the office or at home. Install TeamViewer Host on an unlimited number of computers and devices. As a licensed user, you have access to them all!
Teamviewer 7 For Mac Free Download
Previous versions:
These downloads are only recommended for users with older licenses that may not be used with the latest release of TeamViewer.
See previous versions
Supported operating systems

How To Put Banks On Omnisphere 2

- How To Put Banks On Omnisphere 2 4
- How To Put Banks On Omnisphere 2016
- How To Put Banks On Omnisphere 2 0
- Free Wavsupply Omnisphere Banks
Please note: This video was created on a Mac (OS X 10.8.5) designed to mainly assist Mac OS X 10.7 (and higher) users with locating their 'hidden' Users - Library folder. The video and guide then goes through where to place the additional patches so they are detected in Omnisphere.
Look it up on google, but you basically find the STEAM folder that omnisphere pulls its data from, and paste those patches in the folder you want in “patches” - “presets” or something along those lines, then you need to go in omnisphere and press.install omnisphere in the menu and it’ll refresh and it should have your third party presets.
- Recently purchased omnisphere 2.5 (Mac), everything is working properly except only like 15 of my 100+ 3rd party banks are showing up. Before downloading 2.5, they all worked fine. After downloading the new version I put my banks into LibraryApplication SupportSpectrasonicssteamomnispheresettings librarypatches just like before.
- Omnisphere 2 Install Instructions Installing Patches Open Omnisphere and click on the ‘UTILITY’ button and select ‘Install.omnisphere’ as seen in the Screenshot below: Continue to locate your ‘.omnisphere’ for the specific Patch or Bundle you have purchased. Open the file and your installation is complete!
- Omnisphere 2.6 includes a stunning new “Hardware Library” with over 1,600 new patches created by Eric Persing and the renowned Spectrasonics Sound Development team. Each hardware profile has a corresponding set of sounds in the Hardware Library which were specially designed using that hardware synth as an Omnisphere controller.
- Recently purchased omnisphere 2.5 (Mac), everything is working properly except only like 15 of my 100+ 3rd party banks are showing up. Before downloading 2.5, they all worked fine. After downloading the new version I put my banks into LibraryApplication SupportSpectrasonicssteamomnispheresettings librarypatches just like before.
Windows PC users can still follow this video to see where to place your additional patches. However you will just need to ensure you have located your Spectrasonics folder and then follow the guide / video from here or please view below.
Overview of Video and Guide Details:
Download your purchased expansion library with the Time+Space Connect installer - for ease select your Desktop when asked where you would like to place these files.
Once the download is finished, open the downloaded contents folder into a window.
For Mac users - To locate the CORRECT location to place your files, from within the Finder menu (across the top of your screen) select 'Go'.
With the Go 'drop-down' menu up on the screen hold down your 'alt' key on your keyboard to 'unhide' the Library folder.
How To Put Banks On Omnisphere 2 4
Select the Library folder and double-click the 'Application Support' folder.
Where to place the Patches:
Now locate your 'Spectrasonics' folder and go to 'STEAM', 'Omnisphere', 'Settings Library'.

Here you will find a 'Patches' and a 'Multis' folder.
Double-click the 'Patches' folder.
From your desktop, double-click your downloaded folder to open it into a second window.

Place the two windows next to each other so you can see both windows - your 'Patches' folder and your new content folder.
Within the 'Patches' folder, create a new folder and name it after the developer of the library (ILIO, Audiority or The Unfinished). Now double-click this new folder to open it.
Now simply highlight the new patches folders from the second window and drag&drop them into your new folder.
Please note - the Audiority bundle (Trapshere library) also includes bonus Wav files. These are just for your use, Omnisphere does not need them. You can place them with your usual sound library files if you wish.
Please note - The Unfinished libraries contain 'Patches' presets and 'Multis' presets. Please ensure you place the PATCHES into this Patches folder and then go back to the 'Omnisphere' 'Settings Library' window to locate your 'Multis' folder. Then just create a new folder in here called 'The Unfinished' and drag&drop the additional MULTIS into this folder. This stage is not covered in the video.
Now the files are in the correct location. Open Omnisphere in your DAW / music host.
When the Omnisphere interface loads, please press the 'CHECK FOR UPDATES' button (top-left) and ensure all green lights are showing and that you have installed all of the needed updates. Without the latest update, some presets may not work correctly!
From the Patch Browser within Omnisphere, go to 'Directory' and select your new patches.
If the developer folder does not show, try refreshing the Omnisphere browser window (with the bottom-left circular arrow button).
Where can I purchase Omnisphere 2?
Download sales and Upgrades are now available for purchase in our Webstore/Techshop. Physical sales (boxed with USB drive) are handled exclusively through our Authorized Resellers.
If I already own Omnisphere, is there an Upgrade to Omnisphere 2?
Yes! If you already are an Omnisphere customer, you are eligible for the Omnisphere 2 Upgrade - available now in the Webstore/Techshop.
If I already own Atmosphere, is there an Upgrade to Omnisphere 2?
Yes! If you already are an Atmosphere customer, you are eligible for the Omnisphere 2 Legacy Upgrade - available now in the Webstore/Techshop.
Is there a DEMO version of Omnisphere 2 I can try?
Because of the size of our instruments, we don't offer Demo versions. However, you can contact one of our local dealers in your area in order to arrange a live demo of Omnisphere 2. To find a local dealer in your area, please contact your local Authorized Reseller.
How are Spectrasonics Instruments delivered to new users?
All Spectrasonics instruments are available in two different editions: Boxed and Download. The physical boxed editions now contain high quality USB drives and are sold exclusively to new customers through our Authorized Resellers. The download editions are now available and sold exclusively through our Webstore/Techshop.
Aren’t Spectrasonics Instruments delivered on DVD-ROMS?
They used to be, but this is no longer the case. All our physical boxed versions have now been revised with high-quality USB drives. For convenience, we now also offer download sales of new Spectrasonics Instruments direct to customers from our Webstore/Techshop. Both of these new delivery platforms offer much faster and more reliable installations than DVD discs.
If I buy the Boxed version, will I also be able to get a download in the future? If I buy the Download Edition, will I also be able to get a drive? If I have the DVD-ROM edition, will I be able to get the drive or future downloads if I need them?
Yes to all of the above! We are happy to announce that there are now alternative forms of installation available optionally to registered users - no matter which edition you have originally purchased.
Spectrasonics is keenly aware that many users no longer have computers with optical drives and there are numerous scenarios when the convenience of downloading or the speed of a USB drive would be a preferred form of installation for different types of users. To address all the various user needs and scenarios, Spectrasonics has a new Support Services area that offers Alternative Installation USB Drives and Additional Download Installations for optional purchase. These services are available for purchase in our Webstore/Techshop for registered users.
How is the Upgrade delivered? Is it downloadable? How big?
The Omnisphere 2 Upgrade package is a 60GB download which you can order through Webstore/Techshop.
Is the Omnisphere 2 Upgrade available as a physical product?
Not at this time. Our download service is highly reliable though... even with slower connections.
Can I download the upgrade?
Yes. The upgrade is now exclusively available as a download in our Webstore/Techshop.
Does an Omnisphere 1 license need to be registered and authorized in my Spectrasonics User Account in order to qualify for the Omnisphere 2 Upgrade?
Yes.
Does Omnisphere 1 need to be installed on my computer before purchasing and installing the upgrade to Omnisphere 2?
No. Upgrading to Omnisphere 2 will supply the complete 60GB Omnisphere 2 sound library, which includes the sounds from Omnisphere 1. If Omnisphere 1 is already installed, you will not lose any custom user-created sounds or third-party libraries.
Do I need to have Atmosphere installed before purchasing the upgrade to Omnisphere 2?
No, but if you are an Atmosphere user you will need to have it authorized and registered to qualify for the Legacy upgrade.
Is there a student discount price for Omnisphere 2?
Spectrasonics doesn't offer student discounts, however qualifying schools and institutions can participate in our EDU program.
Does Spectrasonics allow for used sales/license transfers of Omnisphere 2?
Please see the License Transfer FAQs area of the Knowledgebase for more info on our License Transfer Policy.
Can I upgrade if I bought a used copy of Omnisphere v1?
Yes, but only if that copy of Omnisphere has been properly license transferred through Spectrasonics.
Can I upgrade if I bought a used copy of Atmosphere?
Yes, but only if that copy of Atmosphere has been properly license transferred through Spectrasonics.
If I upgrade my Atmosphere to Omnisphere 2 can I later resell and transfer the license of either instrument used to someone else?
No. Customers who participate in a special upgrade program for any Spectrasonics virtual instruments are not eligible for license transfers either for the original instrument or its subsequent upgrade. For example, if an original owner of Atmosphere takes advantage of our special “legacy” upgrade program to Omnisphere 2, the owner is not permitted to resell either instrument and no license transfer will be granted.
If I upgrade my Omnisphere v1 to Omnisphere 2 can I later resell and transfer the license of either instrument used to someone else?
Since it is the same original license, Omnisphere 2 would still be eligible for a future license transfer. However, Omnisphere 1 cannot be transferred as a separate product.
Are Omnisphere 1 and Omnisphere 2 different instruments/products?
No. Omnisphere 2 is simply the next major version of Omnisphere.
Is Omnisphere 2 a Stand-alone app or a Plugin?
Omnisphere 2 includes a standalone application and VST/AU/AAX plug-in platforms that work in all the major DAWs and hosts.
What is the STEAM engine?
STEAM™ is our in-house core technology that is the foundation of Omnisphere, Trilian and a new generation of Spectrasonics instruments.
So does Omnisphere replace Atmosphere?
Yes, Omnisphere is Atmosphere's successor.
What are the minimum system requirements for Omnisphere 2?
You can view them HERE.
Is it compatible with xxx?
Check our Compatibility FAQs in the Knowledgebase which we keep up to date with the latest info.
Will Omnisphere 2 replace my Omnisphere plug-in?
Yes. Omnisphere 2 is the next version of Omnisphere. When installed, the Omnisphere 2 Upgrade contents (20GB) merge with the existing Omnisphere 1 library and become one product, replacing Omnisphere 1 as a plug-in.
When opening older projects which use sounds from Omnisphere 1, will they load the same?
Absolutely - it is still Omnisphere! Version 2 is fully backwards compatible with version 1 projects.
Will custom saved patches/multis be negatively affected when upgrading to Omnisphere 2?
No. They will open and operate the same as always.
Will third party patches be negatively affected when upgrading to Omnisphere 2?
No. All third-party Omnisphere v1 libraries are fully compatible with Omnisphere 2.
Does Omnisphere 2 use Copy Protection?
Yes, please see the Copy Protection FAQs area of the Knowledgebase for more information on our system.
Does Omnisphere 2 include a manual?
All our instruments include a comprehensive online Reference Guide, which is accessible directly through the plug-in. The integrated Reference Guide is searchable and we can keep it up to date with the software releases. You can check out the Reference Guide HERE.
How fast of a computer will I need to run Omnisphere 2?
As with all virtual instruments - the faster the better. Omnisphere 2 is designed to run optimally on modern computers. See the System Requirements for more information.
Does Omnisphere 2 need more CPU power than Omnisphere v1?
Not significantly more. Some newer patches require more resources than older ones. However, many new patches do not require more resources.
Does Omnisphere 2.5 need more CPU power than Omnisphere 2.4?
Not significantly more. Some newer patches require more resources than older ones. However, many new patches do not require more resources.
Is Omnisphere 2 compatible with 32-bit and 64-bit systems?
Omnisphere 2.4 and earlier are compatible with both 32-bit and 64-bit systems. Omnisphere 2.5 and higher are compatible exclusively with 64-bit systems.
How To Put Banks On Omnisphere 2016
Can I easily switch back and forth between Omnisphere 2.5 and Omnisphere 2.4?
Yes! We have a rollback installer that’s easy to use for this purpose if you are unsure if you are ready for 2.5 or not.
Does Omnisphere 2 use streaming?
Yes! Omnisphere 2 streams from the drive for quick loading of the sounds. Drive streaming is configurable as well.
Can I selectively install parts of the Omnisphere 2 library since it is so large?
Because of patch compatibility, Omnisphere 2 must always be installed with the complete library. However, you can install the 60 Gigabyte library to a secondary or external drive if you wish.
Will Omnisphere 2's streaming benefit from a faster hard drive?
Fast drives are a smart way to go of course. There's a chapter in the Reference Guide devoted to optimizing Performance with Omnisphere 2.
How To Put Banks On Omnisphere 2 0
Can I install Omnisphere 2 on a different drive?
Yes, you can definitely install the library to a secondary or external drive.
Can I Use My Own Audio in Omnisphere 2?
Yes! You can now use any WAV or AIFF audio files in Omnisphere as soundsources for creating your own amazing sounds! Omnisphere 2 supports bit depths up to 24-bit files and sample rates up to 192kHz.
Will the audio import in Omnisphere 2 be for single audio files or multi-samples?
Omnisphere 2 supports one audio file of any length per soundsource. You can layer up to four soundsources in a patch and 8 patches in a multi. Keep in mind that Omnisphere's focus is as a synthesizer and will never be a sampler with multiple velocities, key-mapping, round-robin, etc. - there are other instruments out there that do that very well.
Free Wavsupply Omnisphere Banks
Omnisphere 2 allows you to easily turn your audio files and even your audio tracks/mixes into synthesis source for Omnisphere 2's powerful oscillators. It's remarkable how much you can creatively mangle one sound and transform it into something awesome!

Generate Private Key From Pem

The private key is already in PEM format and can be used as-is. – Michael Hampton Jul 16 '15 at 18:59 @MichaelHampton, this will depend on the version of ssh-keygen and the command used to generate the key. Here is an article form Siteground regarding managing private keys on their servers. Take a look at this article for more information on private key locations on common server platforms. If you can't locate your private key, you can generate a new CSR and then rekey your GoDaddy certificate to continue the installation process. Save the combined file as yourdomainname.pem. The.pem file is now ready to use. Creating a.pem with the Private Key and Entire Trust Chain. Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (yourdomainname.crt). Windows - convert a.pem file to a.ppk file. Start PuTTYgen, and then convert the.pem file to a.ppk file. For detailed steps, see Convert Your Private Key Using PuTTYgen. Windows - convert a.ppk file to a.pem file. Start PuTTYgen. For Actions, choose Load, and then navigate to your.ppk file. Choose the.ppk file, and then choose Open.
-->With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
Note
VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.
Supported SSH key formats
Generate Private Key From Pem File Java
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example:
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.
The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Private Key Bitcoin
Next steps
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.
.pem SSL Creation Instructions
SSL .pem files (concatenated certificate container files), are frequently required for certificate installations when multiple certificates are being imported as one file.
This article contains multiple sets of instructions that walk through various .pem file creation scenarios.
Creating a .pem with the Entire SSL Certificate Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt), Root (TrustedRoot.crt), and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Server and Intermediate Certificates
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Private Key and Entire Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Private Key - your_domain_name.key
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN RSA PRIVATE KEY-----
(Your Private Key: your_domain_name.key)
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
